What Is Vulnerability Assessment and Penetration Testing (VAPT)?
Jul 22, 2022In the precarious times of today, where cyber vulnerability is at an upsurge, taking deterrent measures to protect our digital identity is essential more than ever. Data breaches, leakes and other varied forms of threat to data is every web entity’s nightmare. Vulnerability assessment and Penetration Testing (VAPT) then are crucial methodologies to keep cyber threats at bay. In this blog, we will delve deep to understand what Vulnerability assessment and Penetration Testing is and why is it important for your enterprise?
What is VAPT?
When put into simple words, there are two ways of testing vulnerability of a system;
-
- Vulnerability Assessment
- Penetration Testing
Both the tests have different approaches and strengths but are rudimentarily combined together to achieve more comprehensive analysis for vulnerability. Though they yield different results, their area of focus is the same.
While Vulnerability Assessment tools discover which vulnerabilities are present in the system, they however do not differentiate between the flaws that are exploitable to cause damage and those that cannot. A typical vulnerability scanner alerts about the pre existing flaws in the code and where they are located.
On the other hand, Penetration Testing exploits the vulnerabilities present in a system to determine whether any unauthorized access or other malicious activity is possible, therefore identifying which flaws pose a threat to the application and which do not. Penetration tests discover all those exploitable flaws and measure the severity of each. In short, a penetration test shows how damaging a flaw could be in case of a real attack rather than finding every flaw in the system.
What are the Features of VAPT?
A penetration test has the following characteristics:
- It simulates real-world attacks.
- It explores vulnerabilities in systems, networks and applications.
- It discovers the innate cause of the cyber attacks and controls it.
- It provides mitigation of the vulnerabilities found.
- It provides a risk management guideline for companies.
- It helps the companies in the better deployment of security resources.
What are the types of VAPT practices adopted?
There are 3 types of VAPT practices done as follows:
White Box Testing
In this test, the tester provides the server information, network details, operating system details, application details, protocols, etc. to the client. The main purpose of this test is to discover the threats occurring internally in the company, i.e. the threat coming from the organization’s employees.
Black Box Testing
In this test, the tester does not provide any prior information regarding the networks, applications, or systems. The main purpose of this test is to determine the threats occurring externally, and how external hackers can weaponize them to invade your systems.
Hybrid Testing
This test is a mixture of both white-box testing and black-box testing where first the tester performs the black box testing on your systems, followed by the white box testing.
What is the scope of VAPT?
The scope of VAPT distinguishes the assets that are to be scanned and the ones that are to be left. The scope is determined at the planning stage of a divested VAPT, and the entire process runs adhering to it.
The methodology of VAPT is such that testing the web application focuses on gathering public information about the web app and then continuing to map out the network involved in hosting the web app. Investigating for probable injection tampering attacks and the very learning and handling of the application in reality comes later.
What is the process of VAPT? – VAPT Steps
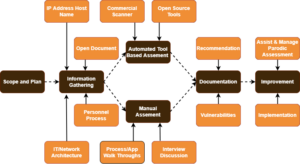
Step 1: Information Gathering
Information gathering, also known as the reconnaissance phase, is one of the most important steps in any vulnerability and penetration testing process since it extends in-depth analysis and information to identify vulnerabilities easily and curtail them later.
There are 2 types of reconnaissance depending on the type of interaction one wishes to achieve with the targeted system:
- Active Reconnaissance
- Passive Reconnaissance
Step 2: Research and Exploitation
There are several security tools for performing web app penetration testing and the best part is that, majority of them are open source.
However, narrowing down those many choices to just a few tools is extremely challenging. Therefore, the reconnaissance phase carries such great importance. It aids you in finding all the necessary information you need to detect vulnerabilities and solve them later on, in addition to narrowing down the attack vectors, so that you can use specific tools to accomplish your goal.
Step 3: Reporting and Recommendations
The structure of the report must be clear and concise with an adequate amount of data to support your findings, while emphasizing on what methods worked in a brief manner.
Writing down and categorizing the successful exploits based on their criticality helps the enterprise to channelize its efforts on fixing the most critical parts of the system.
Step 4: Remediation and Ongoing Support
Many companies face difficulty in remediating all the vulnerabilities that the penetration test revealed. At such juncture, it is best to mitigate critical and high vulnerabilities first and focus on the medium and low afterward.
Tip: Prioritization is the key in cases where the criticality of vulnerability being exploited varies.
While there are certain vulnerabilities that can not be detected without the previous access to the internal system, there are some vulnerabilities that carry the risk of remote code execution and should be adequately prioritized at all cost to assess the likelihood and impact of the same. Many VAPT service providers offer a re-test as part of their contract to extend a secondary penetration test for verifying the mitigated vulnerabilities detected in the previous test.
Why does your enterprise need VAPT?
Vulnerability Assessment and Penetration Testing (VAPT) provides organizations with the most comprehensive evaluation of a particular application than any single test alone. Using the VAPT approach gives an organization a more detailed outlook of the threats their application is prone to, enabling the business to safeguard its systems and data from malicious attacks. Though vulnerabilities are detected in applications from third-party vendors and internally made software, most of these flaws can be easily curtailed once found.
VAPT protects your organization by detecting security weaknesses and guidance to address them. It is increasingly important for organizations aspiring to achieve compliance with standards such as the GDPR, ISO 27001 and PCI DSS.
What is the role of a VAPT service provider?
A pen tester’s objective is to exploit vulnerabilities which might break into a computer system and document how their objective was achieved in a report so that the client can remediate the exploitable vulnerabilities discovered.
Employing a VAPT provider enables the IT security teams to focus on mitigating the critical vulnerabilities while the VAPT provider continues to discover and classify vulnerabilities.
Several organizations employ the services of a professional VAPT service provider for the following reasons:
- To find and fix vulnerabilities before they are suspected by an attacker.
- To help uncover vulnerabilities of which the existence was unknown.
- To assess the damage to the business in terms of impact in case of an attack becomes successful.
- To find out how effectively the organization can detect and respond to an attack.
- As an annual exercise to evaluate how and where they stand in the ever-changing global cyber security landscape.
- To evaluate the risk posture and impact analysis of a target system in a live environment.
- To meet necessary compliances with regulatory standards like PCI DSS, GDPR and more.
Penetration testers will work with organizations to tailor the scope of the project, which will define which systems and networks to emphasize upon. An expert team will then treat the vulnerabilities which could have affected your overall business and help you out in coming up with effective solutions. The main objective of our VAPT practitioners is to penetrate the organization’s systems and find and fix those loopholes in all possible means that an actual hacker might use.
Bottom Line
Vulnerability Assessment and Penetration Testing (VAPT) are a broad range of Cyber security assessment services mechanized to help you identify and address the security exposures across your organization’s IT estate.
It is crucial for you to choose the right type of assessment for your company’s needs, and we can help you understand the various types of VAPT services and the differences between them. Our diverse nature of VAPT assessments that vary significantly in depth, breadth, scope and price, ensure each test delivers the best value for your money. Contact us for more about our VAPT and penetration testing services.




